山东大学软件工程应用与实践——GMSSL开源库(九)——SM9密钥封装与公钥加密的源代码分析
2021SC@SDUSC文章目录int SM9_wrap_key(密钥的封装)int SM9_unwrap_key(密钥的解封)int SM9_encrypt(公钥加密算法)int SM9_decrypt(解密算法)小结为了便于理解,在把流程图再次贴在每一个函数标题下。int SM9_wrap_key(密钥的封装)参数定义:int ret = 0;EC_GROUP *group = NULL;EC
2021SC@SDUSC
文章目录
为了便于理解,在把流程图再次贴在每一个函数标题下。
int SM9_wrap_key(密钥的封装)
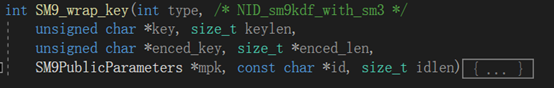

参数定义:
int ret = 0;
EC_GROUP *group = NULL;
EC_POINT *Ppube = NULL;
EC_POINT *C = NULL;
EVP_MD_CTX *md_ctx = NULL;
BN_CTX *bn_ctx = NULL;
BIGNUM *r = NULL;
BIGNUM *h = NULL;
fp12_t w;
const EVP_MD *kdf_md;
const EVP_MD *hash1_md;
const BIGNUM *p = SM9_get0_prime();
const BIGNUM *n = SM9_get0_order();
unsigned char cbuf[65];
unsigned char wbuf[384];
unsigned char dgst[64];
int all;
确定kdf_md使用的是哪种类型的杂凑函数:
switch (type) {
case NID_sm9kdf_with_sm3:
kdf_md = EVP_sm3();
break;
case NID_sm9kdf_with_sha256:
kdf_md = EVP_sha256();
break;
default:
SM9err(SM9_F_SM9_WRAP_KEY, SM9_R_INVALID_DIGEST_TYPE);
return 0;
}
计算g
if (!rate_pairing(w, NULL, Ppube, bn_ctx)) {
SM9err(SM9_F_SM9_WRAP_KEY, SM9_R_RATE_PAIRING_ERROR);
goto end;
}
确定hash1使用的是那种杂凑函数
switch (OBJ_obj2nid(mpk->hash1)) {
case NID_sm9hash1_with_sm3:
hash1_md = EVP_sm3();
break;
case NID_sm9hash1_with_sha256:
hash1_md = EVP_sha256();
break;
default:
SM9err(SM9_F_SM9_WRAP_KEY, ERR_R_SM9_LIB);
goto end;
}
计算Qb= H1(ID_B||hid) * P1 + Ppube,同时确定hash1使用的杂凑函数:
if (!SM9_hash1(hash1_md, &h, id, idlen, SM9_HID_ENC, n, bn_ctx)
|| !EC_POINT_mul(group, C, h, NULL, NULL, bn_ctx)
|| !EC_POINT_add(group, C, C, Ppube, bn_ctx)) {
ERR_print_errors_fp(stderr);
SM9err(SM9_F_SM9_WRAP_KEY, ERR_R_EC_LIB);
goto end;
}
在k不是全0的条件下进行流程图第2、3、4、5、6步的计算:
do {
if (!BN_rand_range(r, n)) {
goto end;
}
} while (BN_is_zero(r));
/* C = r * Q_B */
if (!EC_POINT_mul(group, C, NULL, C, r, bn_ctx)
|| EC_POINT_point2oct(group, C, POINT_CONVERSION_UNCOMPRESSED,
cbuf, sizeof(cbuf), bn_ctx) != sizeof(cbuf)) {
SM9err(SM9_F_SM9_WRAP_KEY, ERR_R_EC_LIB);
goto end;
}
/* w = g^r */
if (!fp12_pow(w, w, r, p, bn_ctx) || !fp12_to_bin(w, wbuf)) {
SM9err(SM9_F_SM9_WRAP_KEY, SM9_R_EXTENSION_FIELD_ERROR);
goto end;
}
/* K = KDF(C||w||ID_B, klen) */
while (outlen > 0) {
if (!EVP_DigestInit_ex(md_ctx, kdf_md, NULL)
|| !EVP_DigestUpdate(md_ctx, cbuf + 1, sizeof(cbuf) - 1)
|| !EVP_DigestUpdate(md_ctx, wbuf, sizeof(wbuf))
|| !EVP_DigestUpdate(md_ctx, id, idlen)
|| !EVP_DigestUpdate(md_ctx, counter, sizeof(counter))
|| !EVP_DigestFinal_ex(md_ctx, dgst, &len)) {
SM9err(SM9_F_SM9_WRAP_KEY, ERR_R_EVP_LIB);
goto end;
}
if (len > outlen)
len = outlen;
memcpy(out, dgst, len);
out += len;
outlen -= len;
counter[3]++;
}
all = 0;
for (len = 0; len < keylen; len++) {
all |= key[len];
}
} while (all == 0);
int SM9_unwrap_key(密钥的解封)


参数定义:
int ret = 0;
EC_GROUP *group = NULL;
EC_POINT *C = NULL;
EVP_MD_CTX *md_ctx = NULL;
BN_CTX *bn_ctx = NULL;
point_t de;
fp12_t w;
const BIGNUM *p = SM9_get0_prime();
const EVP_MD *kdf_md;
unsigned char wbuf[384];
unsigned char *out = key;
size_t outlen = keylen;
unsigned char counter[4] = {0, 0, 0, 1};
unsigned char dgst[64];
unsigned int len;
接下来是跟封装时一样的确定kdf所使用的密码杂凑函数的类型,在此不再赘述。
确定C是否属于G1
/* parse C on E(F_p) */
if (!EC_POINT_oct2point(group, C, enced_key, enced_len, bn_ctx)) {
SM9err(SM9_F_SM9_UNWRAP_KEY, ERR_R_MALLOC_FAILURE);
goto end;
}
/* parse de on E'(E_p^2) */
if (!point_from_octets(&de, ASN1_STRING_get0_data(sk->privatePoint), p, bn_ctx)) {
SM9err(SM9_F_SM9_UNWRAP_KEY, ERR_R_MALLOC_FAILURE);
goto end;
}
计算w ‘= e(C, de)
if (!rate_pairing(w, &de, C, bn_ctx)) {
SM9err(SM9_F_SM9_UNWRAP_KEY, ERR_R_MALLOC_FAILURE);
goto end;
}
if (!fp12_to_bin(w, wbuf)) {
SM9err(SM9_F_SM9_UNWRAP_KEY, ERR_R_MALLOC_FAILURE);
goto end;
}
计算K = KDF(C||w||ID_B, klen)
while (outlen > 0) {
if (!EVP_DigestInit_ex(md_ctx, kdf_md, NULL)
|| !EVP_DigestUpdate(md_ctx, enced_key + 1, enced_len - 1)
|| !EVP_DigestUpdate(md_ctx, wbuf, sizeof(wbuf))
|| !EVP_DigestUpdate(md_ctx, ASN1_STRING_get0_data(sk->identity), ASN1_STRING_length(sk->identity))
|| !EVP_DigestUpdate(md_ctx, counter, sizeof(counter))
|| !EVP_DigestFinal_ex(md_ctx, dgst, &len)) {
SM9err(SM9_F_SM9_UNWRAP_KEY, ERR_R_EVP_LIB);
goto end;
}
int SM9_encrypt(公钥加密算法)


参数定义:
int ret = 0;
SM9Ciphertext *sm9cipher = NULL;
int kdf;
const EVP_MD *md;
unsigned char *key = NULL;
size_t keylen;
unsigned char C1[1 + 64];
size_t C1_len;
unsigned char mac[EVP_MAX_MD_SIZE];
unsigned int maclen = sizeof(mac);
int len;
size_t i;
确定不同的type。
由于这里默认使用的是sm3密码杂凑函数,故源码中把sha256的case给注释掉了。同时,无论是否使用sms4与简单的xor异或操作或者cbc或ctr等不同的分组加密工作模式,只要使用的是sm3的密码杂凑函数,给kdf与md赋上值即可。
switch (type) {
case NID_sm9encrypt_with_sm3_xor:
kdf = NID_sm9kdf_with_sm3;
md = EVP_sm3();
break;
/*
case NID_sm9encrypt_with_sha256_xor:
kdf = NID_sm9kdf_with_sha256;
md = EVP_sha256();
break;
*/
case NID_sm9encrypt_with_sm3_sms4_cbc:
case NID_sm9encrypt_with_sm3_sms4_ctr:
default:
return 0;
}
计算C1、C2、C3
if (!SM9_wrap_key(kdf, key, keylen, C1, &C1_len, mpk, id, idlen)) {
SM9err(SM9_F_SM9_ENCRYPT, ERR_R_SM9_LIB);
goto end;
}
for (i = 0; i < inlen; i++) {
key[i] ^= in[i];
}
if (!EVP_Digest(key, keylen, mac, &maclen, md, NULL)) {
SM9err(SM9_F_SM9_ENCRYPT, ERR_R_EVP_LIB);
goto end;
}
连接C1、C2、C3,并进行编码
if (!ASN1_STRING_set(sm9cipher->pointC1, C1, C1_len)
|| !ASN1_STRING_set(sm9cipher->c2, key, inlen)
|| !ASN1_STRING_set(sm9cipher->c3, mac, maclen)) {
SM9err(SM9_F_SM9_ENCRYPT, ERR_R_SM9_LIB);
goto end;
}
if ((len = i2d_SM9Ciphertext(sm9cipher, &out)) <= 0) {
SM9err(SM9_F_SM9_ENCRYPT, ERR_R_SM9_LIB);
goto end;
}
int SM9_decrypt(解密算法)


参数定义:
int ret = 0;
SM9Ciphertext *sm9cipher = NULL;
unsigned char *key = NULL;
size_t keylen;
int kdf;
const EVP_MD *md;
const unsigned char *C2;
int C2_len;
unsigned char mac[EVP_MAX_MD_SIZE];
unsigned int maclen = sizeof(mac);
int i;
接下来是与加密相同的类型确定代码,在这里不再赘述,可参考上文源代码中的type的确定方式。
把密文解码
if (!(sm9cipher = d2i_SM9Ciphertext(NULL, &in, inlen))) {
SM9err(SM9_F_SM9_DECRYPT, ERR_R_SM9_LIB);
goto end;
}
C2 = ASN1_STRING_get0_data(sm9cipher->c2);
C2_len = ASN1_STRING_length(sm9cipher->c2);
计算M,C2与K按位异或得到
for (i = 0; i < C2_len; i++) {
out[i] = C2[i] ^ key[i];
}
计算并确定C3
memcpy(key, C2, C2_len);
if (!EVP_Digest(key, keylen, mac, &maclen, md, NULL)) {
SM9err(SM9_F_SM9_DECRYPT, ERR_R_EVP_LIB);
goto end;
}
if (CRYPTO_memcmp(ASN1_STRING_get0_data(sm9cipher->c3), mac, maclen) != 0) {
SM9err(SM9_F_SM9_DECRYPT, ERR_R_EVP_LIB);
goto end;
}
小结
以上源代码在GMssl源码库中的\GmSSL-master\crypto\sm9\sm9_enc.c中可以找到。
在源代码阅读分析的过程中,可以看出国标文件中的流程图指导着源代码的编写。源代码每一步的流程,都在上文流程图中可以找到相应的步骤。一步一步,代码比较精炼紧凑,代码的封装性较好。通过一段时间的阅读GMSSL源代码,逐步的对其封装的变量和函数调用的接口有所了解,此次代码阅读起来没有多大难度。
如有错误,欢迎批评指正!

DAMO开发者矩阵,由阿里巴巴达摩院和中国互联网协会联合发起,致力于探讨最前沿的技术趋势与应用成果,搭建高质量的交流与分享平台,推动技术创新与产业应用链接,围绕“人工智能与新型计算”构建开放共享的开发者生态。
更多推荐
 已为社区贡献6条内容
已为社区贡献6条内容








所有评论(0)